Getting Started with iOS Penetration Testing, The Setup.

Introduction:
With the increased use of IOS devices in our daily lives, securing these platforms becomes crucial. IOS penetration testing, is the process of identifying and addressing vulnerabilities in IOS applications. In this blog post, will cover what you actually need to get started in this journey of securing IOS applications.
Prerequisites:
To begin pentesting IOS applications, it is important for you to have two things at your disposal:
- A jailbroken iPhone running on IOS version 15.4.1 or lesser
- A Macbook with XCode & iProxy
P.s: You can alternatively use a windows system to perform further activities like jailbreaking your iPhone using: https://ios.cfw.guide/using-palen1x But is good to have a mac to pentest your IOS applications to it’s fullest potential.
Jailbreaking iPhone:
It is important to jailbreak an iphone to enable access to the IOS file system, facilitating in-depth examination of applications and system files, to allow the use of advanced tools like Frida and Cycript for dynamic analysis and real-time manipulation of IOS applications.
Step 1: Identify the IOS version on your iphone and the latest jailbreak available for it using the below guide:
In my case i have an Iphone X with IOS version 15.4.1 running on it, you can find IOS version of your device by visiting Settings > General > About.

At the time of writing this blog, These are the supported jailbreaks for my IOS version:
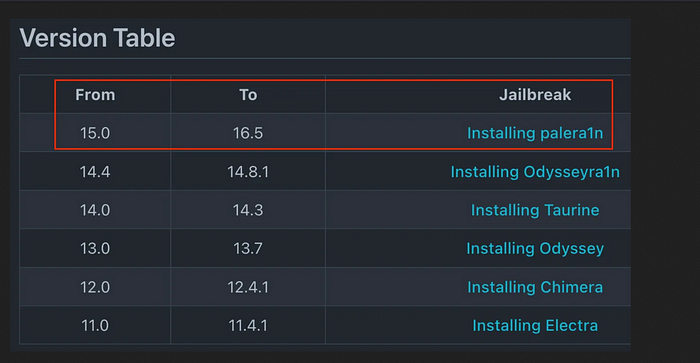
Step 2: Jailbreaking Iphone using palera1n
To jailbreak a device using palera1n we need to ensure two things on our device
- Disable passcode on your iphone
- Enter the device in DFU mode
You can refer this article to know more about DFU mode: https://help.ifixit.com/article/108-dfu-restore
Once this two things are done you can download palera1n from this link :
After Downloading, You can simply run the command “palera1n” from CLI while your device is connected to your mac/windows in DFU mode. It will boot jailbroken post that.

Post jailbreaking you should be able to view palera1n app using which you can install Sileo which is the package manager to install IOS tweaks and tools that we will require to test IOS applications.

Step 3: Adding repos that you need in order to aid you in pentesting IOS applications. To add these you need to go Sources > Click on “+” sign > Add the shown repo URLS in Sileo.

Step 4: Gaining root access to IOS file system using iproxy
Palera1n unlike other jailbreaks uses port 44 for SSH connections for that you need to use a SSH Tunnel over USB tool (iproxy) to gain root access using CLI.
- On one terminal type “sudo iproxy 22 44” while the iphone is connected to your mac, This will create a listener on your iphone for SSH connections.

2. On another terminal type “root@locahost” to obtain root shell of your jailbroken iphone.
By default the root account password is “alpine” on iphones. Once gained the root shell you can start exploring internal system files of your IOS application to examine vulnerabilities which will cover later.

That’s pretty much it that you need to set yourself up for IOS Pentesting.
